Which of the Following Authentication Methods Is 100 Percent Accurate
User id bsmart card cfinger authentiation. Which of the following authentication methods is 100 percent accurate.
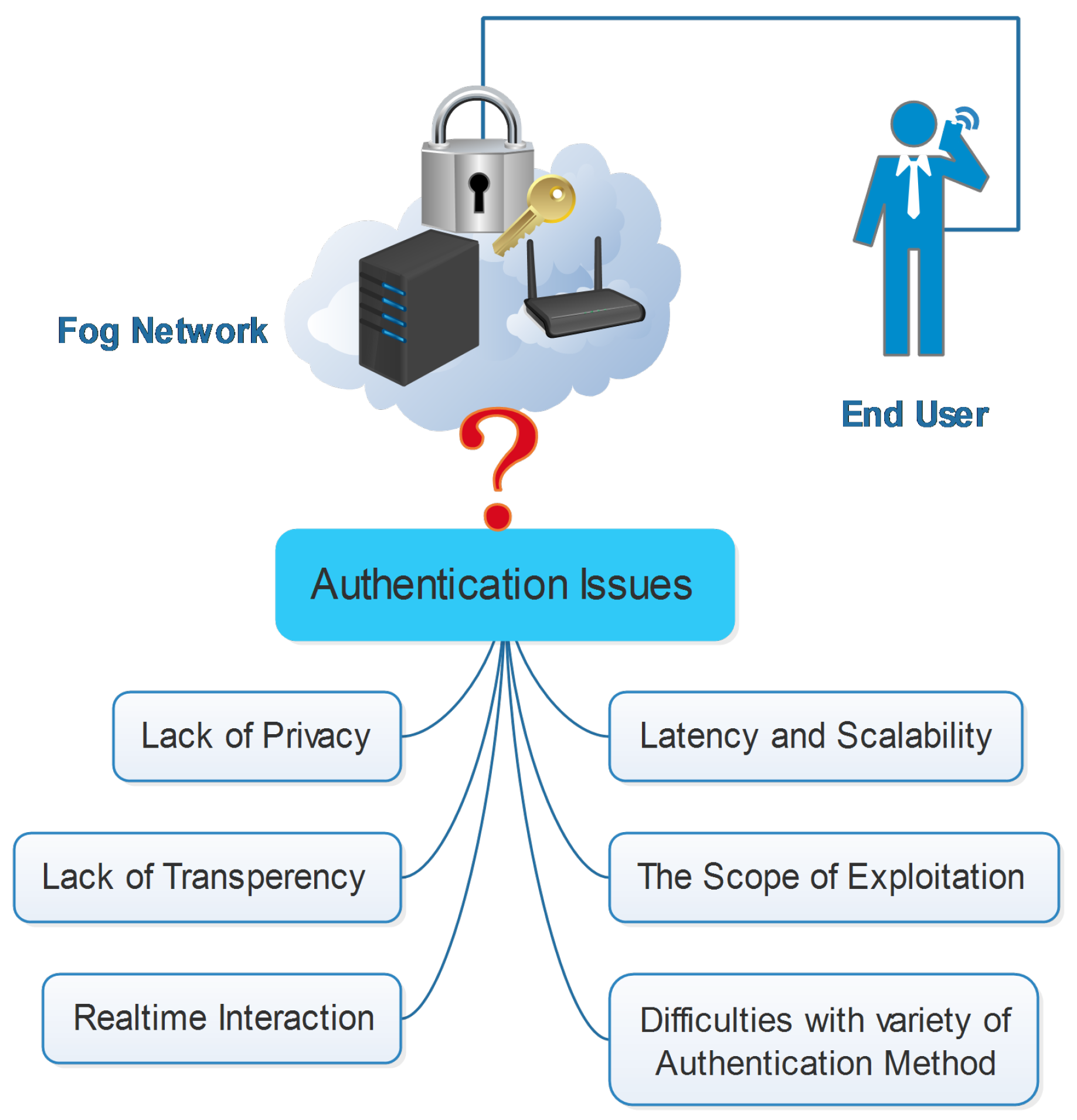
Electronics Free Full Text Towards Secure Fog Computing A Survey On Trust Management Privacy Authentication Threats And Access Control Html
Which of the following authentication methods is being requested.

. Log in to SmartConsole. Voice pattern What is meant by physically constrained user interface. The message sender attaches the certificate and the recipient can verify authenticity with the certificate repository.
User ID Smart card Fingerprint authentication None of the above. Which of the following authentication methods is 100 percent accurate-Fingerprint authentication-Smart card -User ID -None of the above. Hello please post an solution as well 88 Likes report.
The Institute of Electrical and Electronics Engineers. It is never possible to have all of the information required to make a 100 percent accurate prediction. Caroline via iOS.
Courtney via iOS. Username and password internal LDAP C. LEAP is a wireless security method based on 8021X.
Single-factor authentication is when only one authentication factor is used. False Which of these biometric authentication methods is not as accurate as the rest. Lightweight Extensible Authentication Protocol LEAP and Extensible Authentication Protocol EAPFlexible.
In this case Something you know is being used as an authentication factor. Which of the following authentication methods ARE NOT used for Mobile Access. Fingerprints have been used as a form of identification for well over 100 years.
None of the above. Home CompTIA 220-1002 Which of the following authentication methods is being requested. Which of the following authentication methods is 100 percent accurate.
1 March 2020 March 1 2020 exams Leave a comment. Which of the following is least secure method of authentication Key card fingerprint retina pattern Password Answer is Password Comments and Discussions. Which of the following authentication methods is 100 percent accurate.
With biometric authentication this means that you can scan your fingerprint and use it as a type of key to unlock and secure devices. User Datagram Protocol UDP Role-based access control RBAC means limiting users access to database views as opposed to allowing users to access data in database tables directly. Which of the following methods of access authentication and authorization is the MOST secure by defaultAKerberosBTACACSCRADIUSD.
Receive an SMS text message that includes a verification code. Authentication via Secure Tunneling FAST are both authentication methods that were invented by Cisco. RADIUS server B.
What is social engineering. Which of the following authentication methods is 100 percent accurate. A method for confirming users identities.
Which of the following authentication methods is 100 percent accurate. On the Network Security tab select Identity Awareness. Which of the following authentication methods is 100 percent accurate.
One Comment on Which of the following authentication methods can be co. None of these are authentication methods are 100 percent accurate. 159 Which of the following authentication methods is 100 percent accurate.
Username password and PIN form part of Something you. None of the above None of the above authentication methods are 100 percent accurate. Which of the following authentication methods is 100 percent accurate.
Biometrics allows a person to be identified and authenticated based on recognizable and verifiable data unique and specific. Insert a small card in to a desktop computer and provide a PIN code when prompted. A fingerprint authentican b.
Biometric authentication compares data for the persons characteristics to that persons biometric template to determine resemblance. From the left navigation Toolbar click GATEWAYS SERVERS. None of the above.
Home Check Point 156-31580 Which of the following authentication methods ARE NOT used for Mobile Access. Which of the following is not one of the three primary information security areas. Receive a call on a mobile phone and select the pound sign when prompted.
Something that is part of the user such as a fingerprint or voice signature. None of these Fingerprint authentication User ID Smart card. Which of the following authentication methods is 100 percent accurate.
Joe an end user has been prompted to provide his username and password to access the payroll system. Digital certificates are issued by a trusted third party. None of these are correct.
18 September 2020 September 18 2020 exams Leave a comment. A user interface that does not provide. CompTIA question 3304.
Biometrics authentication and identification. There is no other type of authentication that is so readily visible and. Terms in this set 15 What is the most costly and intrusive form of authentication.
After all every single person has a fingerprint that is unique to them. The Identity Awareness Configuration wizard opens. Double-click the Identity Awareness Security Gateway object.
You dont need to login to post your comment. Which of the following authentication methods is Sara using. Your biometrics are often all over the place eg fingerprints or face or can be captured by anyone following you around.
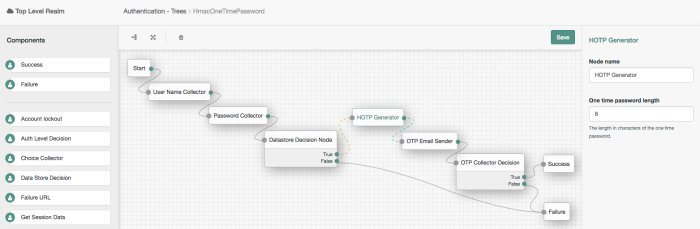
Forgerock Access Management 6 5 Authentication And Single Sign On Guide
What Is The Most Secure Authentication Method Penta Security
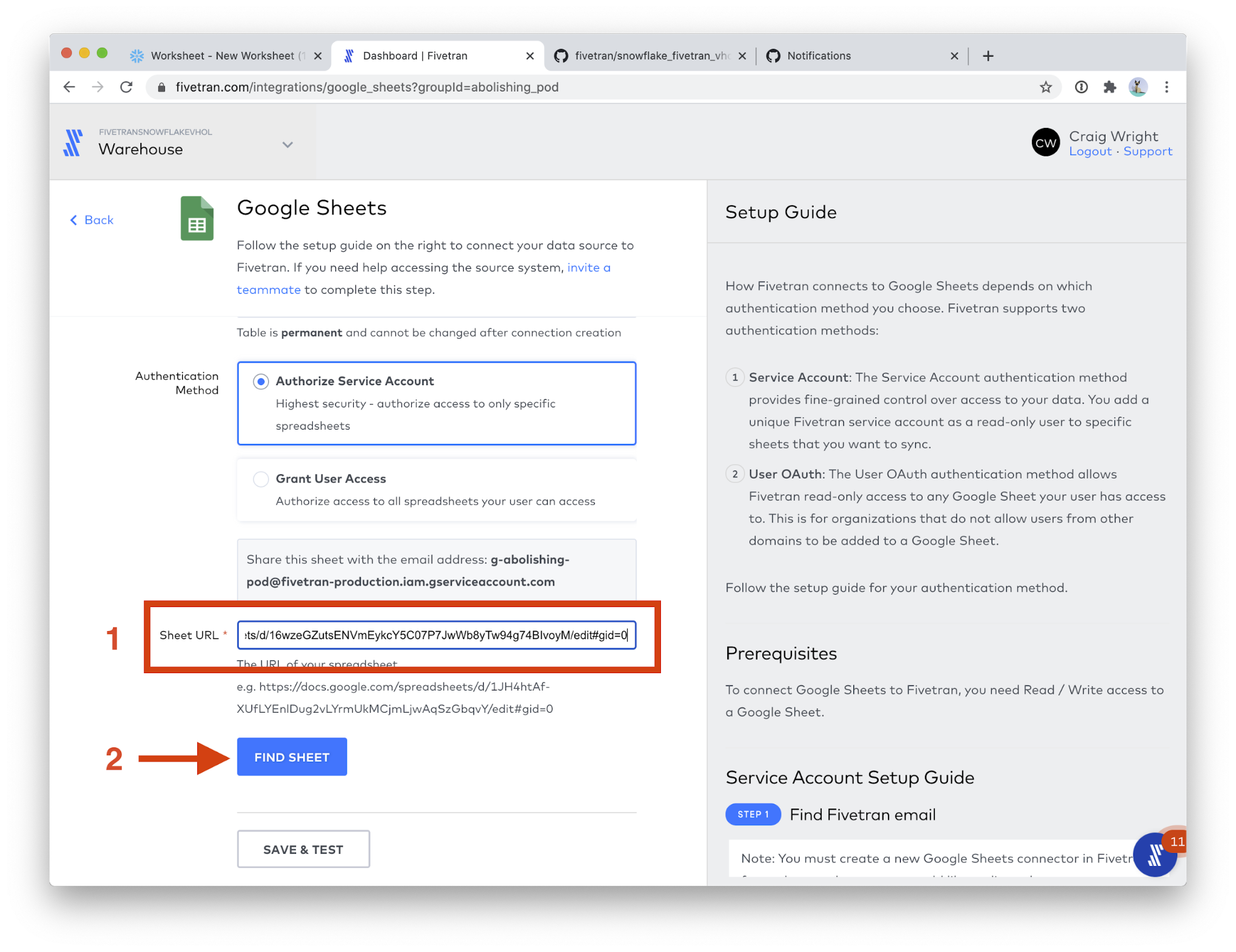
Automating Data Pipelines To Drive Marketing Analytics With Snowflake Fivetran
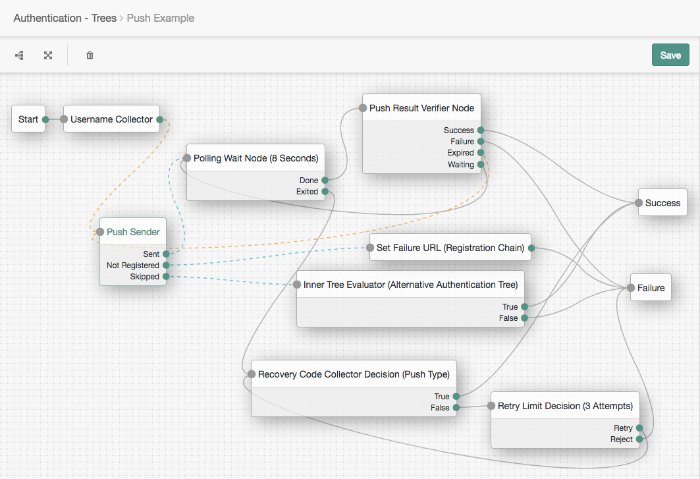
Forgerock Access Management 6 5 Authentication And Single Sign On Guide
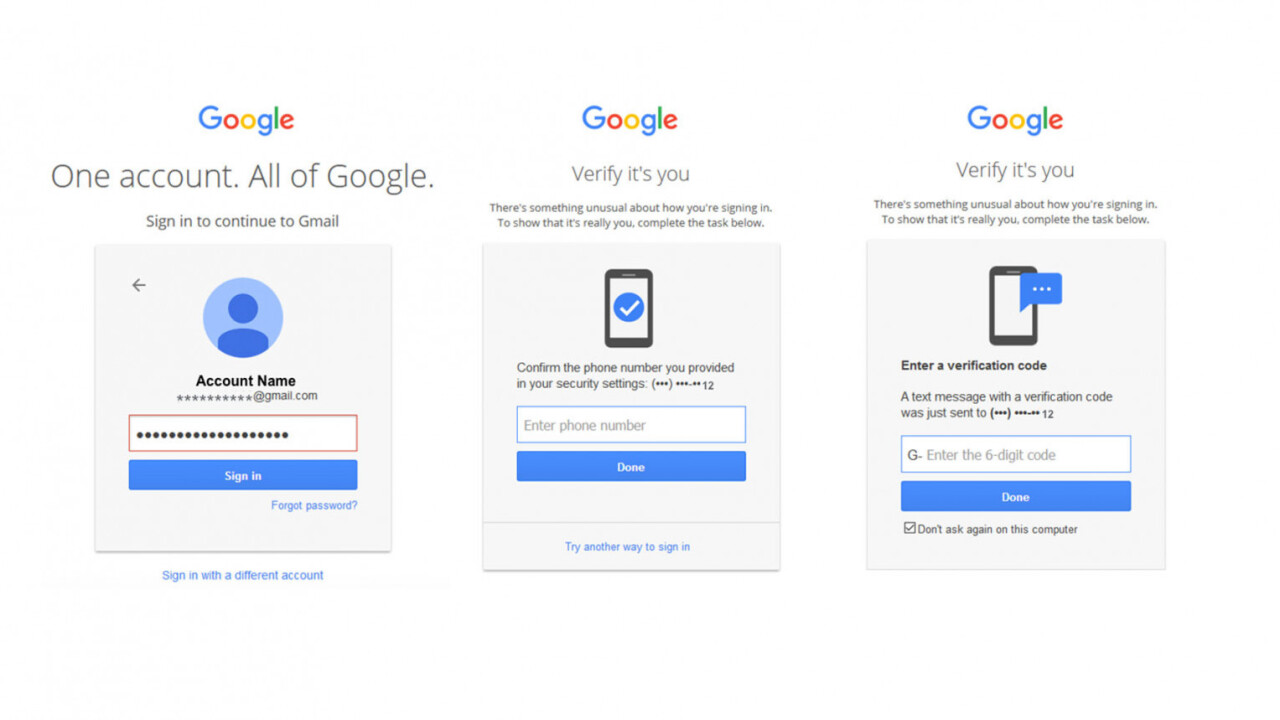
Google Data Shows 2 Factor Authentication Blocks 100 Of Automated Bot Hacks

Askpcmag How Accurate Is The Apple Watch S Heart Rate Monitor Pcmag
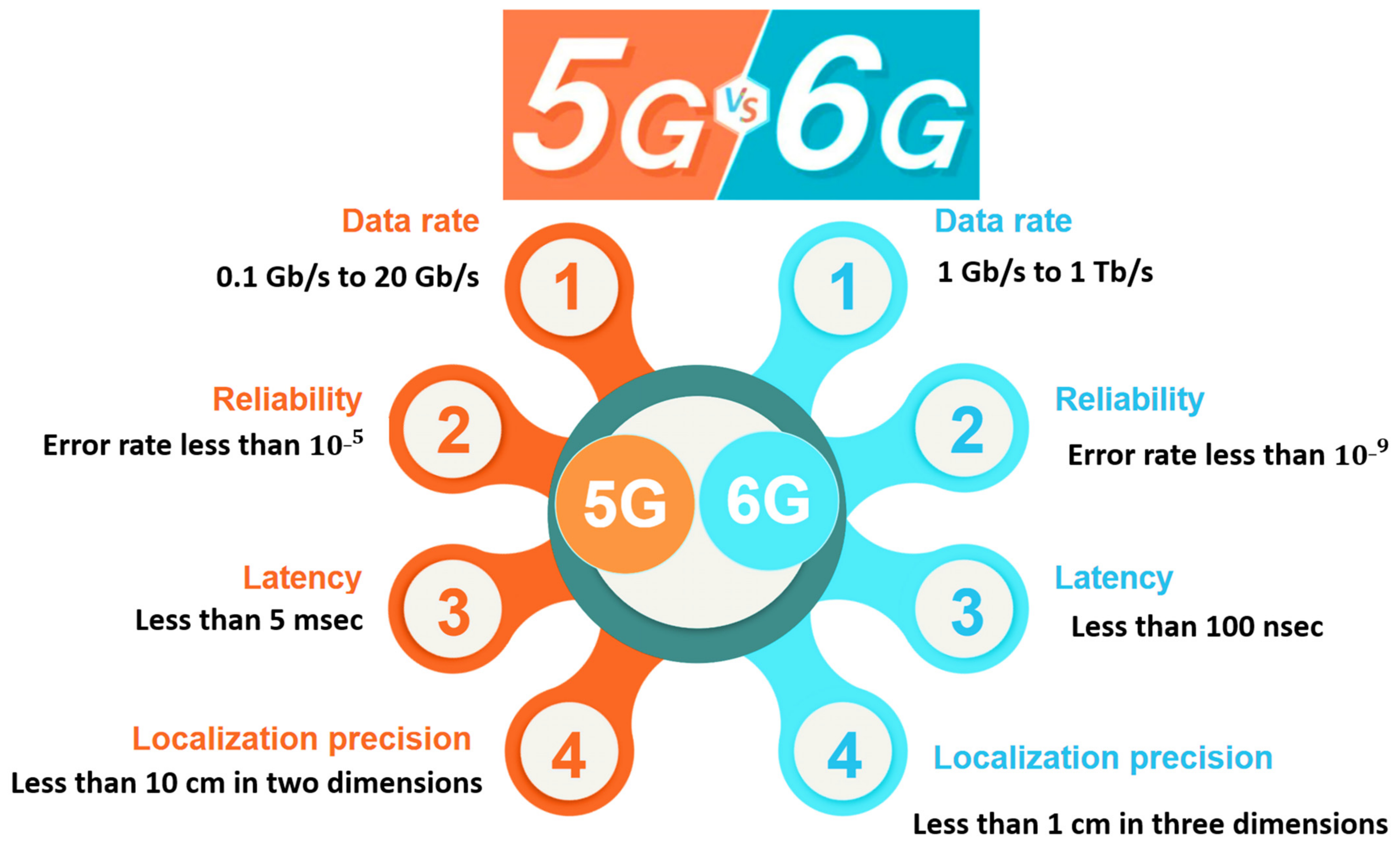
Sensors Free Full Text Security Requirements And Challenges Of 6g Technologies And Applications Html

Mis Chapter 4 Quizzes Flashcards Quizlet

Sensors Free Full Text Ecg Authentication Based On Non Linear Normalization Under Various Physiological Conditions Html

Information Systems Flashcards Quizlet

5 Authentication Methods Putting Passwords To Shame

Crossover Error Rate An Overview Sciencedirect Topics

Verifast Biometric Palm Authentication Technology Brochure Fiserv
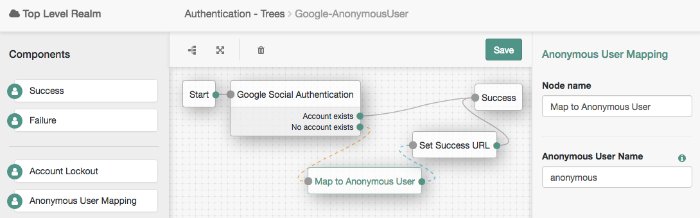
Forgerock Access Management 6 5 Authentication And Single Sign On Guide
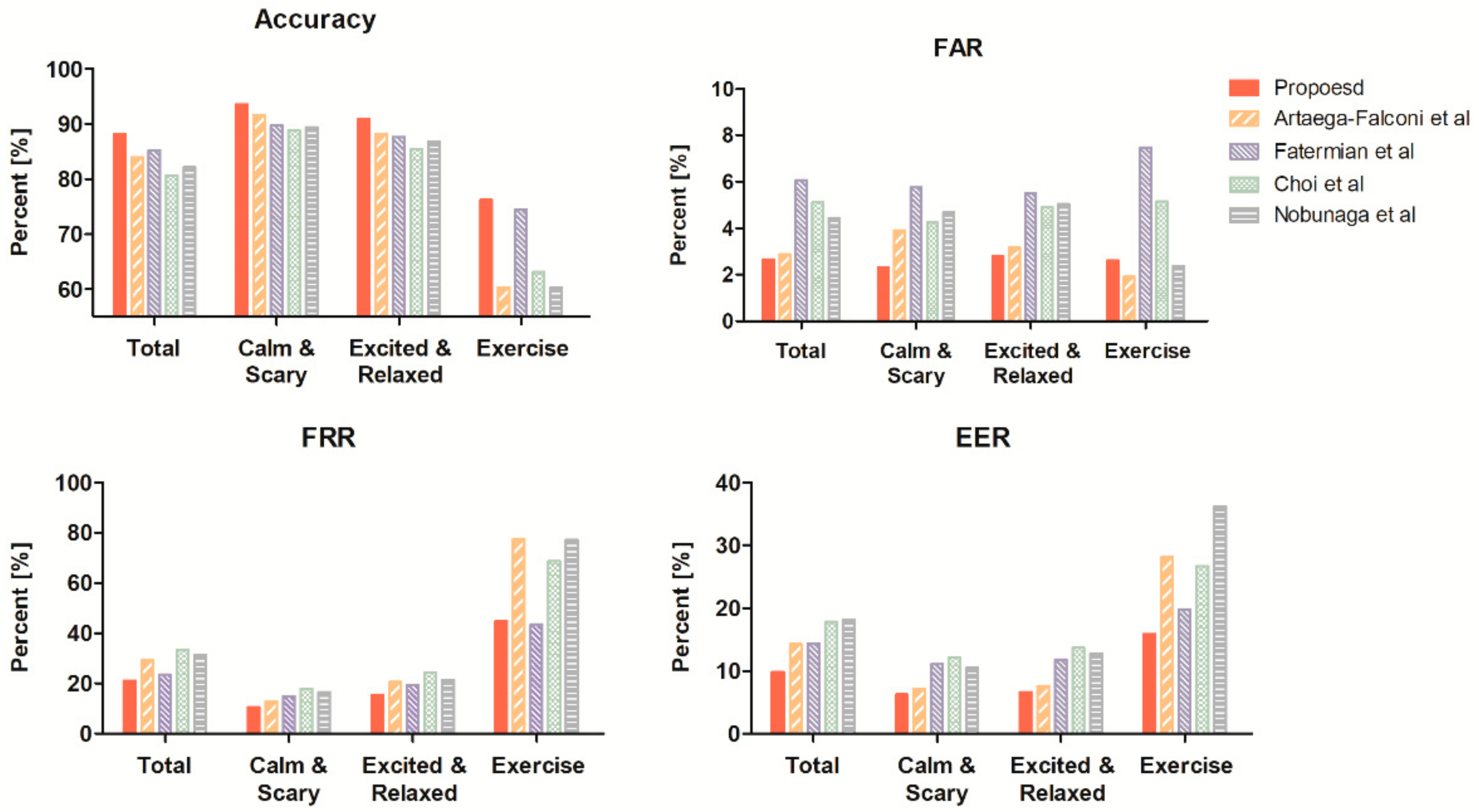
Sensors Free Full Text Ecg Authentication Based On Non Linear Normalization Under Various Physiological Conditions Html

Comments
Post a Comment